Blue Team-System Live Analysis [Part 11]- Windows: User Account Forensics- NTUSER.DAT Rules, Tools, Structure, and Dirty Hives!
Let’s Connect | LinkedIn | Twitter
Without a doubt, the Windows registry is one of the most valuable forensics data sources that investigators can use. I should think of a dedicated series on Windows Registry Forensics, but, for now, we only focus on NTUSER.DAT and its role in user account forensics.
Note: This post only focuses on the NTUSER.DAT, however, the rules and tools can be used for other registry files such as System, Sam, Security, Software, and Default.
Part 10 explained how we could forensically extract one of the most important files to analyse user profiles, settings, and activities. Yes, the NTUSER.DAT. The data stored in NTUSER.DAT and the logs give us fantastic information about each user. As we have them in hand now, let’s explore.
1- Rules First, Tools Next!
You may know the main principle of my writeups: Know the Rules, Before Using Tools. We can be masters of tools, quickly refer to them, and start analyzing our files, nothing wrong with that!
But, in my opinion, dive into how things are working (e.g. file structures, operations, interactions, logic, formats, etc. ) makes us an expert and even helps us understand tools capabilities better.
Example: We may have heard that how amazing is Registry Explorer to deal with windows registry forensics. I do agree with this statement too! Why? Well, let's learn few rules then.
2- Unreconciled data (Dirty Hive!)
The NTUSER.DAT is the primary file for the HKEY_CURRENT_USER hive and keeps user-related information; however, Windows is not updating this file in real-time.
In fact, when a system is running, the data being stored in transaction logs first and will be synced with the primary file when the system is logging off, all the users are inactive, or an hour has elapsed since the last sync.
Part 8 Recap: Windows keep a backup of all the activities and changes such as accessing folders, opening files, network shares, etc., in netuser.dat.LOG1 and netuser.dat.LOG2 during the live session and saves them into NTUSER.DAT during Log off.
- The Challange
The NTUSER.DAT collected from a victim system may not contain the most updated data as we are conducting the live analysis, and the transaction logs data may have not yet been transferred to the primary file.
- The Solution
To address this issue, we need to obtain the netuser.dat.LOG1 and netuser.dat.LOG2 (we did it in part 10 ) and aggregate them with NTUSER.DAT to have all the data in hand.
Wait? How do we know whether the NTUSER.DAT is updated or not!
3- How to Detect dirty hives
Some tools make life easy, but if you ask me, the manual analysis gives us a greater understanding of what we are doing, which is crucial for every investigator.
Don’t get me wrong, what I just suggested must be employed during training and capability development. We are not supposed to avoid tools and waste our time and energy on the battlefield. There are many tools available to have fun, and we will use them right away in a real investigation.
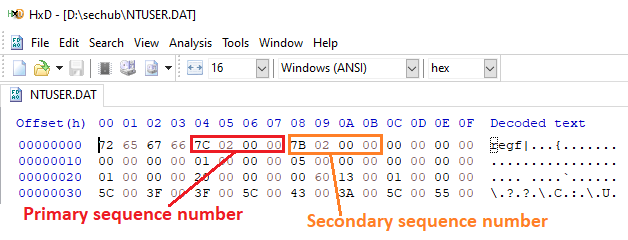
It’s highly recommended to understand the structure of the primary hive. However, to make it simple, we need to check two fields of the NTUSER.DAT header as follows:
- Primary sequence number: This number incremented by 1 when the write operation on NTUSER.DAT begins.
- Secondary sequence number: This number incremented by 1 when the write operation on NTUSER.DAT ends.
The above numbers should be equal in the event of a successful write operation. Thus:
- If the Primary sequence number !=Secondary sequence number: the NTUSER.DAT is not updated (Dirty Hive) and must be aggregated with netuser.dat.LOG1 and netuser.dat.LOG2.
- If the Primary sequence number ==Secondary sequence number: the NTUSER.DAT is updated (Clean Hive) and contains the complete actual data.
Now we have a good idea of why it is important to obtain the netuser.dat.LOG1 and netuser.dat.LOG2 in addition to the primary file. We need them to update the NTUSER.DAT. How? Well, it's time to justify why Registry Explorer is one of the bests!
The main strength of the Registry Explorer tool is the ability to identify the dirty NTUSER.DAT and replay the netuser.dat.LOG1 and netuser.dat.LOG2 to fix the issue.
4- How to Read NTUSER.DAT
There are few paid tools such as OSForesnics and FTK Registry Viewer to work with NTUSER.DAT and registry files in general. We can use demo versions to get familiar with them.
However, Windows built-in commands and free tools such as RegRipper and Registry Explorer are good enough to conduct our investigation.
4.1 Windows built-in command
The reg commands enable us to perform various operations on windows registry subkeys. We need the reg load, reg query, and reg unload commands to work with NTUSER.DAT collected from the test system.
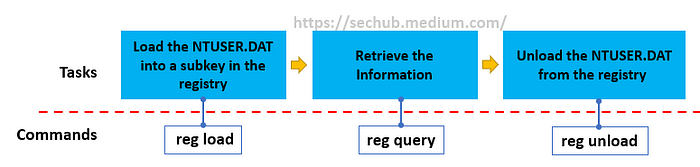
- Load the NTUSER.DAT
We can use the reg load command to load the NTUSER.DAT into a temporary subkey in the Windows registry to view and read it.
reg load HKLM\sechub d:\sechub\NTUSER.datThe above command loads the NTUSER.dat into the sechub subkey under the HKEY_LOCAL_MACHINE that can be viewed in Regedit.

- Retrieve Information
Now we can use the reg query to retrieve desired information from the loaded NTUSER.dat. The figure below depicts the two queries as an example.
reg query HKLM\sechub
and
reg query HKEY_LOCAL_MACHINE\sechub\Environment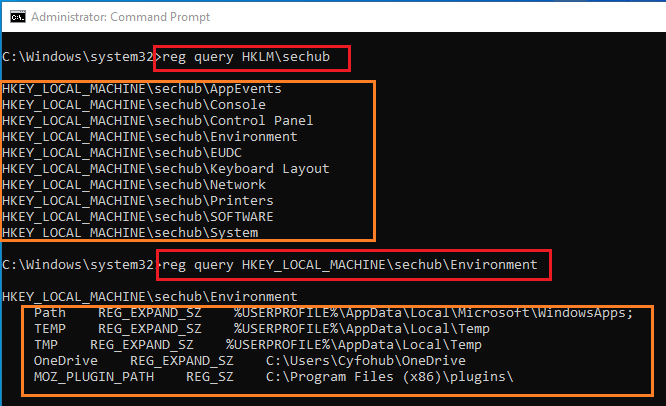
- Unload the NTUSER.DAT
Once we get all the information we look for, we should unload the NTUSER.DAT from the registry and remove the temporary subkey.
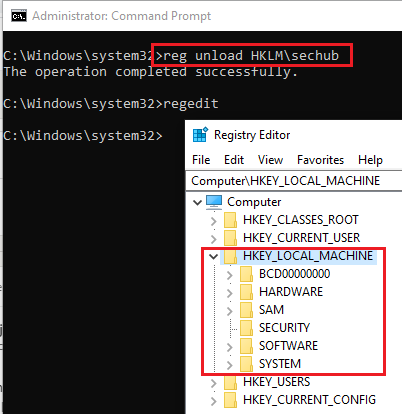
Note: The windows registry must be closed during the load and unload process.
4.2 RegRipper
Working with the RegRipper is quite straightforward; load the NTUSER.DAT as Hive File, set the file name and directory for the report, and we are good to go!
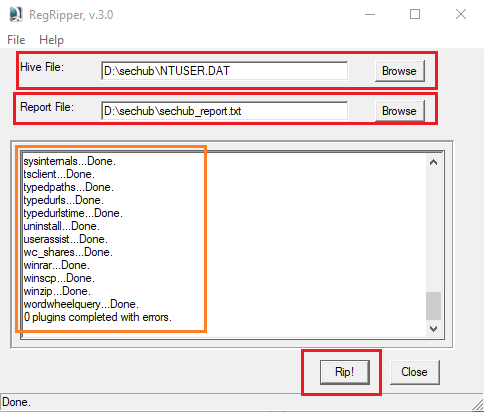
The report will be in txt format as follows:
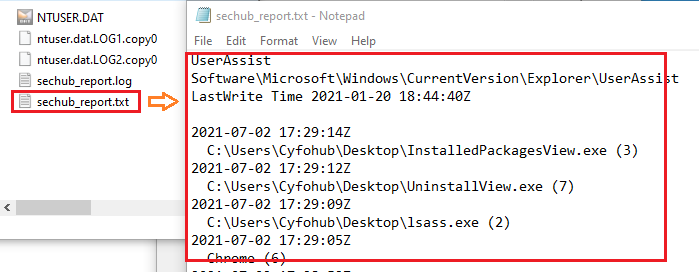
Even though the RegRipper is easy to use, the result will be in plain text that makes data navigation difficult, not a big deal! But, the is a bigger issue.
The RegRipper will not handle the unreconciled data restored in transaction logs (netuser.dat.LOG1 and netuser.dat.LOG2), and as a result, we may not have the most updated data by just analyzing the main file (NTUSER.DAT).
Note: We may have the same issue using the Built-in Command!
4.3 Registry Explorer
It's free and powerful; what else do we want! It is highly recommended to download the tool and give it a try. It has an amazing user manual covering both the GUI based Registry Explorer and RECmd command-line tool.
Load the NTUSER.DAT hive from the file menu:

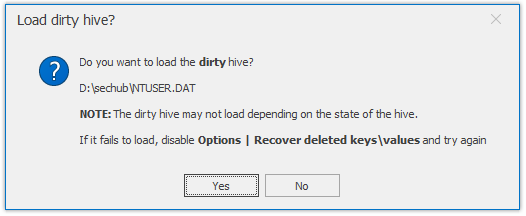
As expected, we will face a warning message that shows that the “primary and secondary sequence numbers do not match. “ Oh.. we know what does it mean!
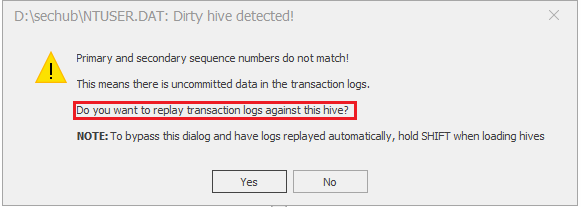
We can also press No and open the NTUSER.DAT as it is, but why would we do that! Let's press yes and replay the transaction logs to update our primary file.

Just click on the ok and select the ntuser.dat.LOG1 and ntuser.dat.LOG2.

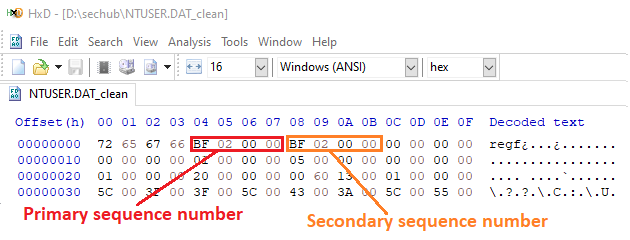
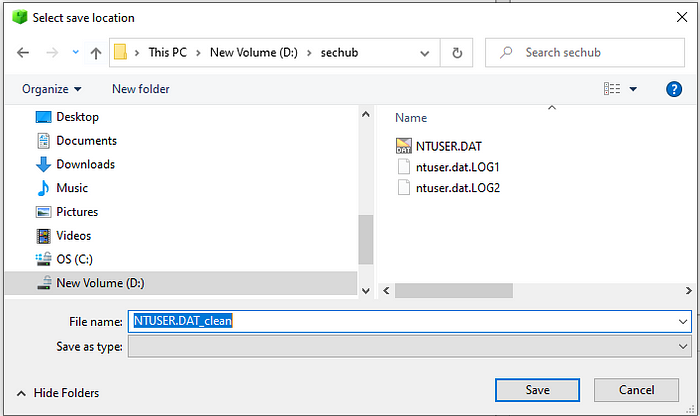
It will be quick, and we need to click the OK button to save the clean (updated) version of the NTUSER.DAT in the desired location.

The NTUSER.DAT_clean name is automatically given to the updated version.
Note: By holding shift while loading the NTUSER.DAT file at the beginning we can shorten the above process and let the logs replayed automatically. However, the updated primary file will reside on memory only and we will not have a copy of clean NTUSER.DAT on the hard disk.
The saved file has exact similar sequence numbers as it's updated now. We can load it later or click on the yes and load it now.
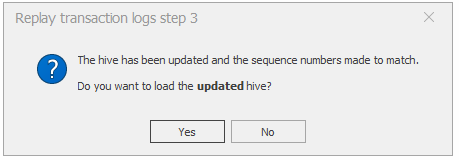
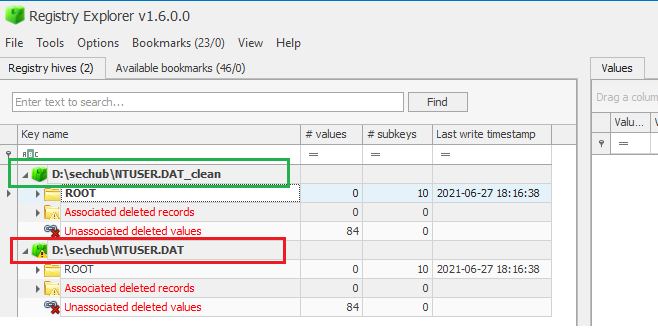
We have an option to open the old file at the same e time to have a comparison.
We can work with both the clean and the dirty hives at the same time:
Done! we can now enjoy the investigation. Are you wondering what we should look for and what we can have by analysing the NTUSER.DAT?
Stay tuned; the next post will discuss the forensics values of the NTUSER.DAT and their locations in the hive.
![Nothing Cyber [NC]](https://miro.medium.com/v2/resize:fill:128:128/1*doB4EEMqeBvfEautz41IPQ.jpeg)